Comprehensive real-time monitoring across your multi-cloud setup
Continuously monitor, detect and prevent misconfigurations and threats in your multi-cloud infrastructure.
Built by the team that has helped secure






Continuously monitor, detect and prevent misconfigurations and threats in your multi-cloud infrastructure.
Built by the team that has helped secure






Cloud environments are becoming more complex with diverse services, granular configurations, authorization policies, and frequent provider updates.
Multi-cloud adoption brings agility, cost efficiency, flexibility, but also introduces challenges in managing a more complex infrastructure and reducing security visibility across vendors.
Fast shipping requirements can strain security teams, creating new cloud resources without adequate configuration or consideration for downstream or connected infrastructure.
Incomplete cloud environment visibility and understanding leads to blind spots, increasing the risk of undetected vulnerabilities and breaches.
Our platform provides instant results through an efficient agentless onboarding process, with read-only access that eliminates cloud costs and agent vulnerabilities associated with the agent-based approach.
Identify exploitable alerts & detect potential threats ensuring maximum coverage and zero false positives with our attacker intelligence approach.
Our cloud security solution continuously scans cloud assets in real-time, providing complete attack surface visibility across multi-cloud infrastructures and eliminating blind spots.
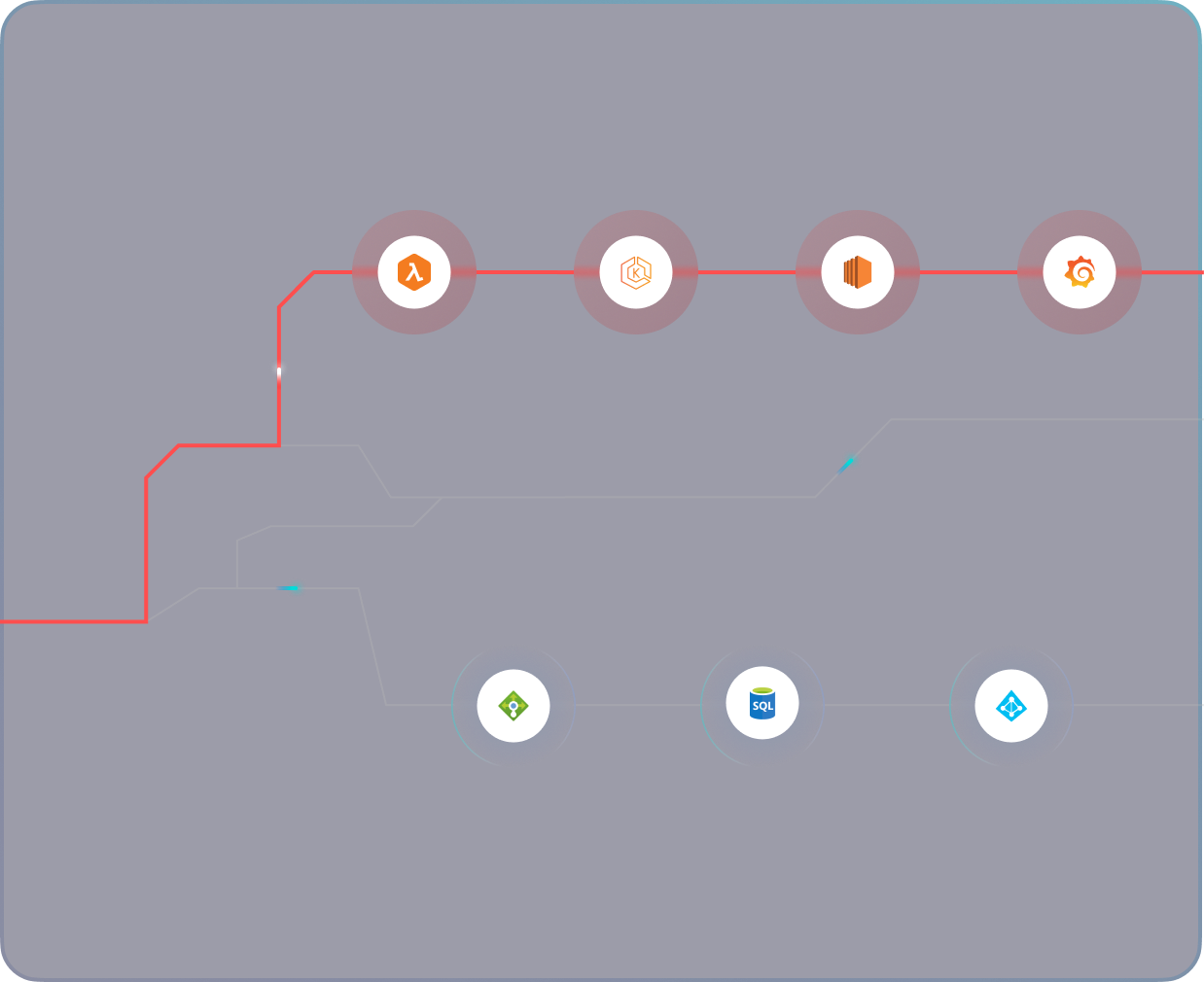
Get context-aware alerts triggered by resource-specific context, providing actionable insights to efficiently and effectively address misconfigurations.
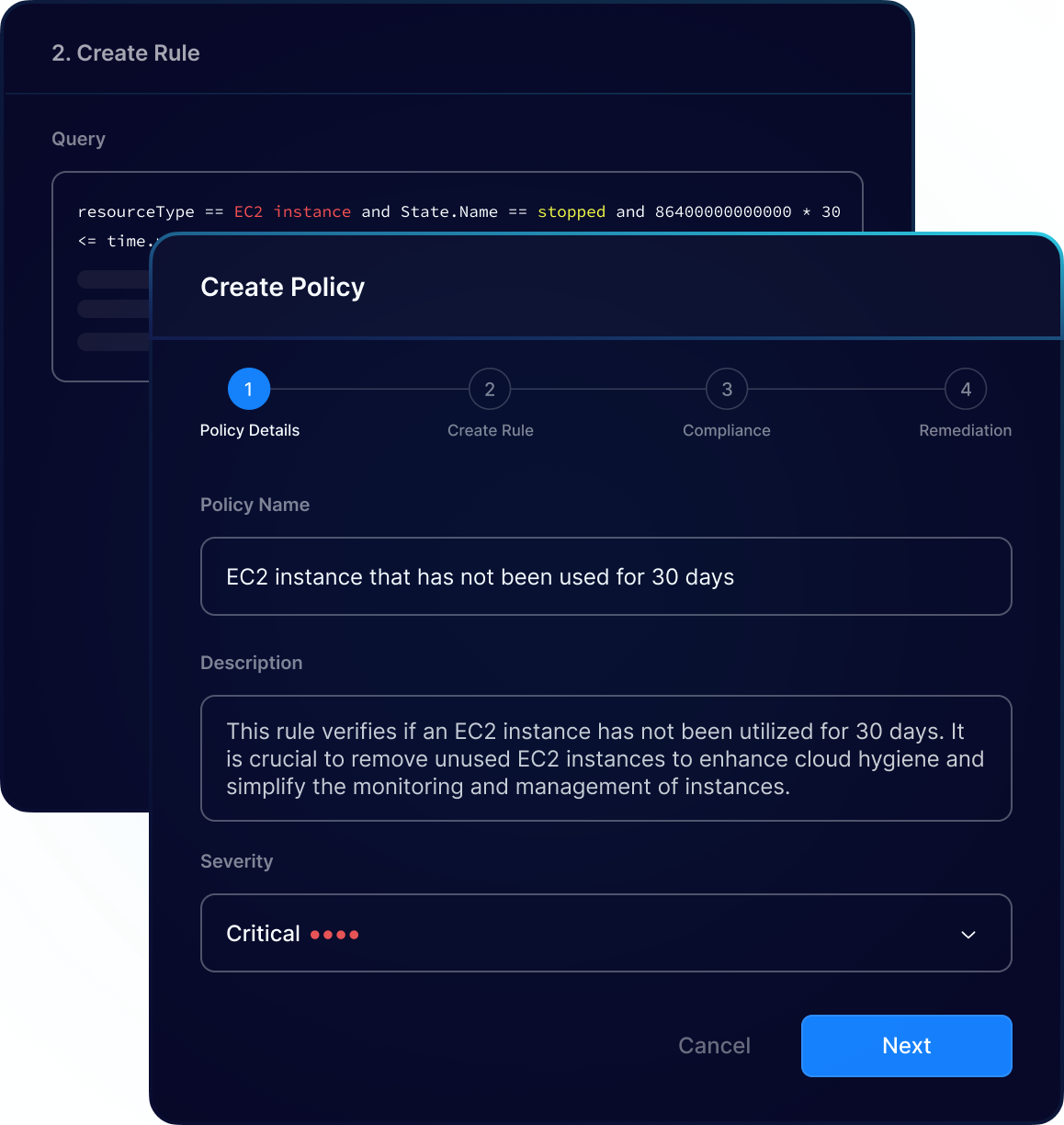
PingSafe’s platform detects and fixes misconfigurations in real-time, ensuring maximum security while minimizing the window of opportunity for attackers.






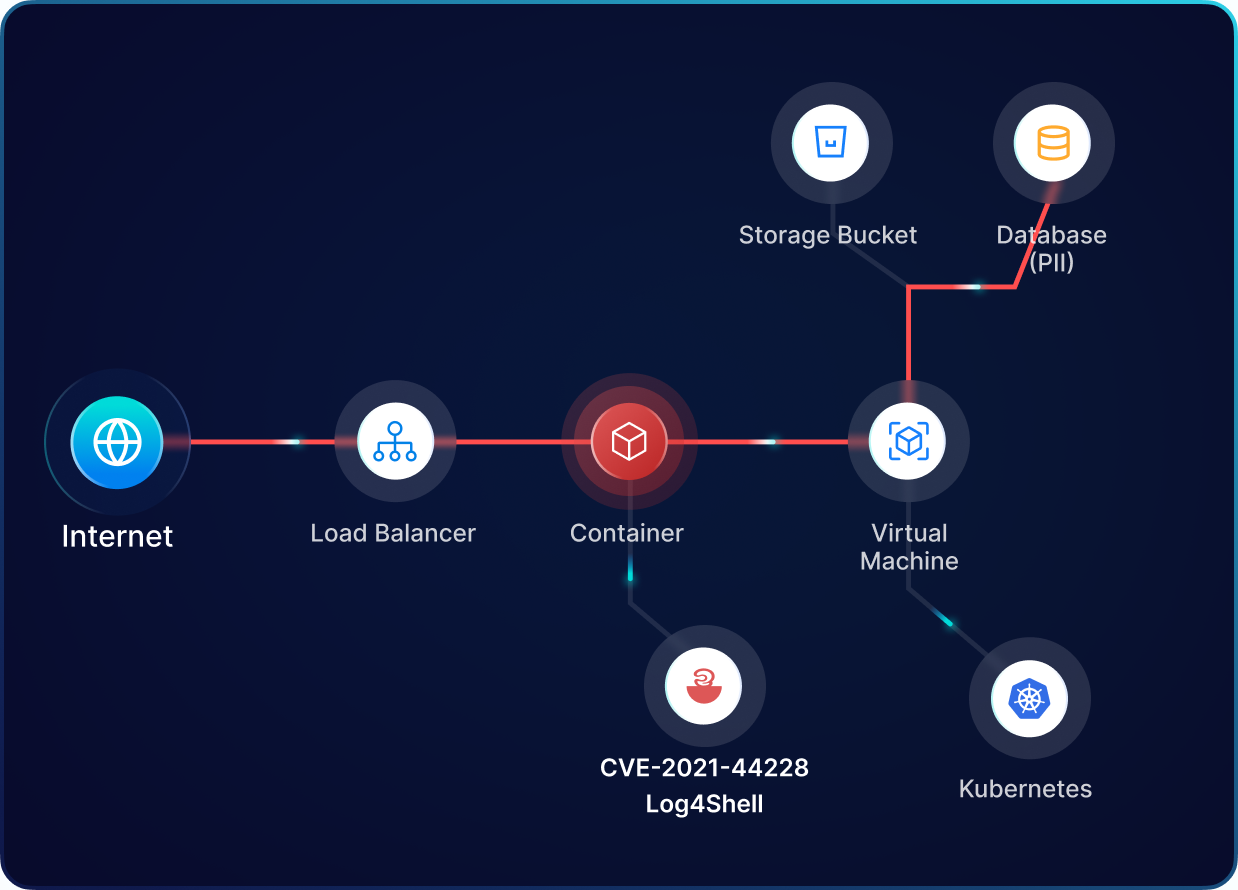
Our cloud security platform provides a holistic view of cloud infrastructure and security posture by understanding resource interlinkages and their potential misconfiguration impact.
PingSafe automatically assesses 1,400+ configuration rules, ensuring the detection of cloud misconfigurations across different runtime environments (GCP, Azure, AWS, Digital Ocean), providing a centralized view and easy management/monitoring.
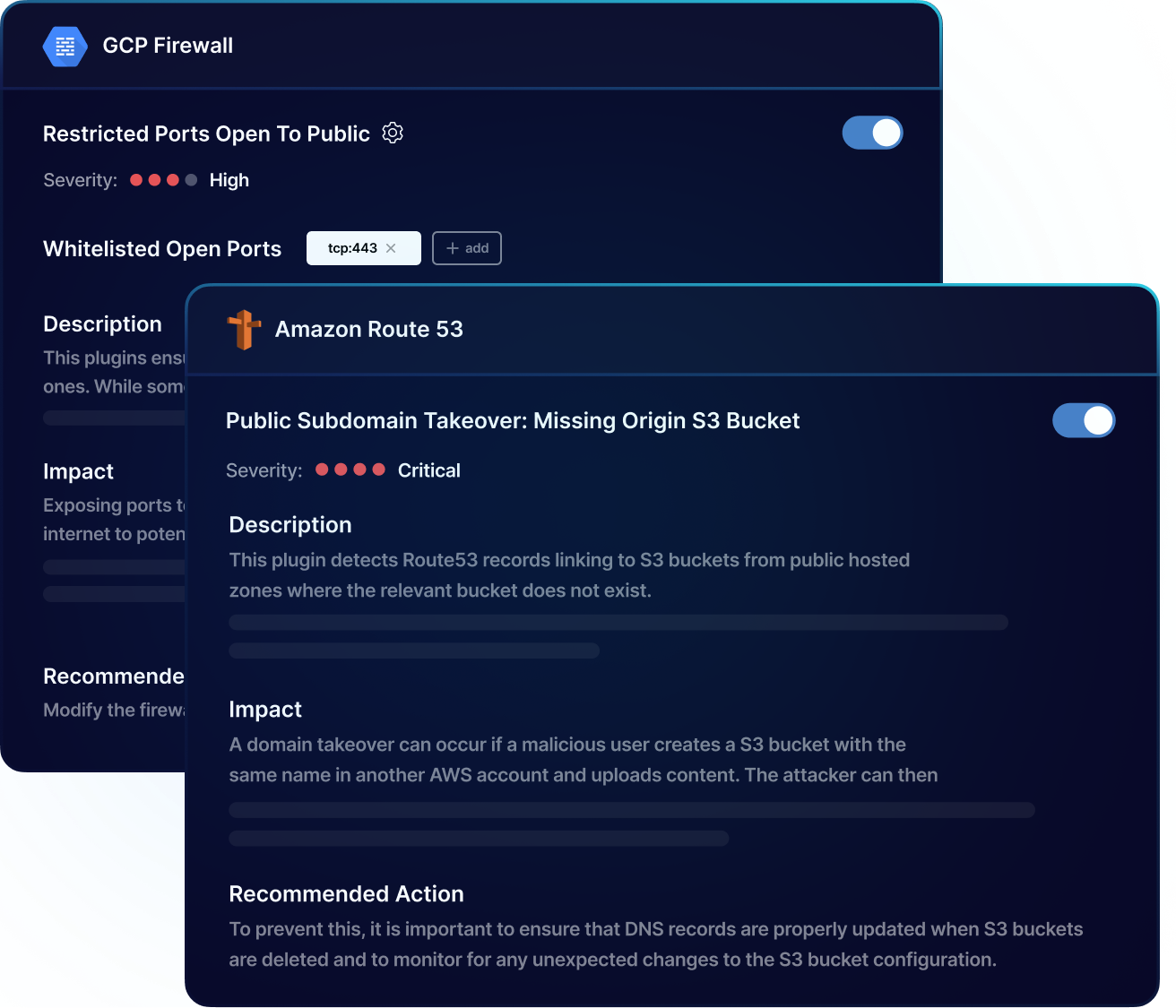
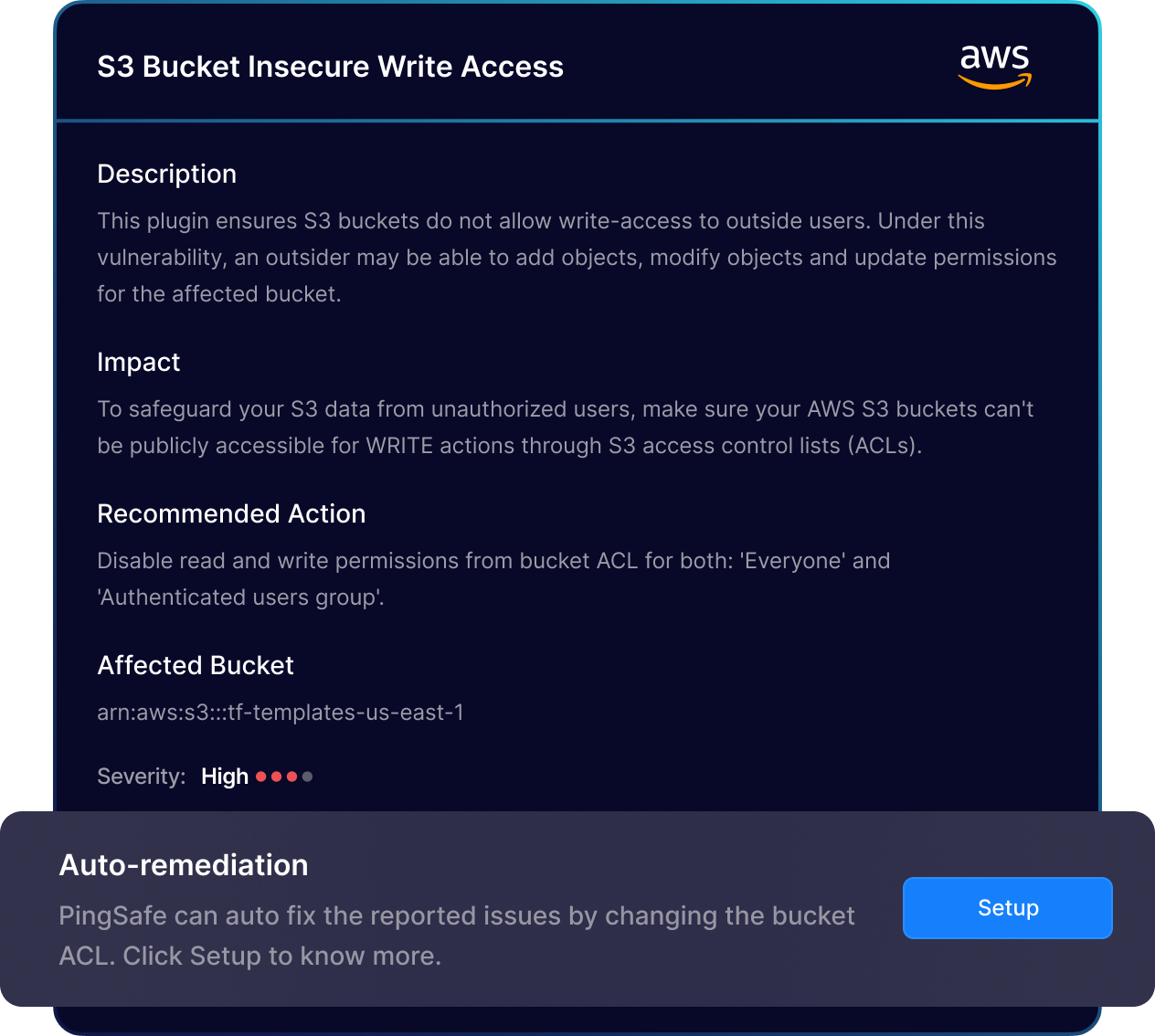
Continuously monitor your cloud infrastructure using advanced algorithms to identify misconfigurations in near real-time, triggering automatic remediation workflows for 24/7 security and compliance.
PingSafe allows organizations to create custom policies aligned with their unique security requirements, safeguarding sensitive data and resources against potential threats.