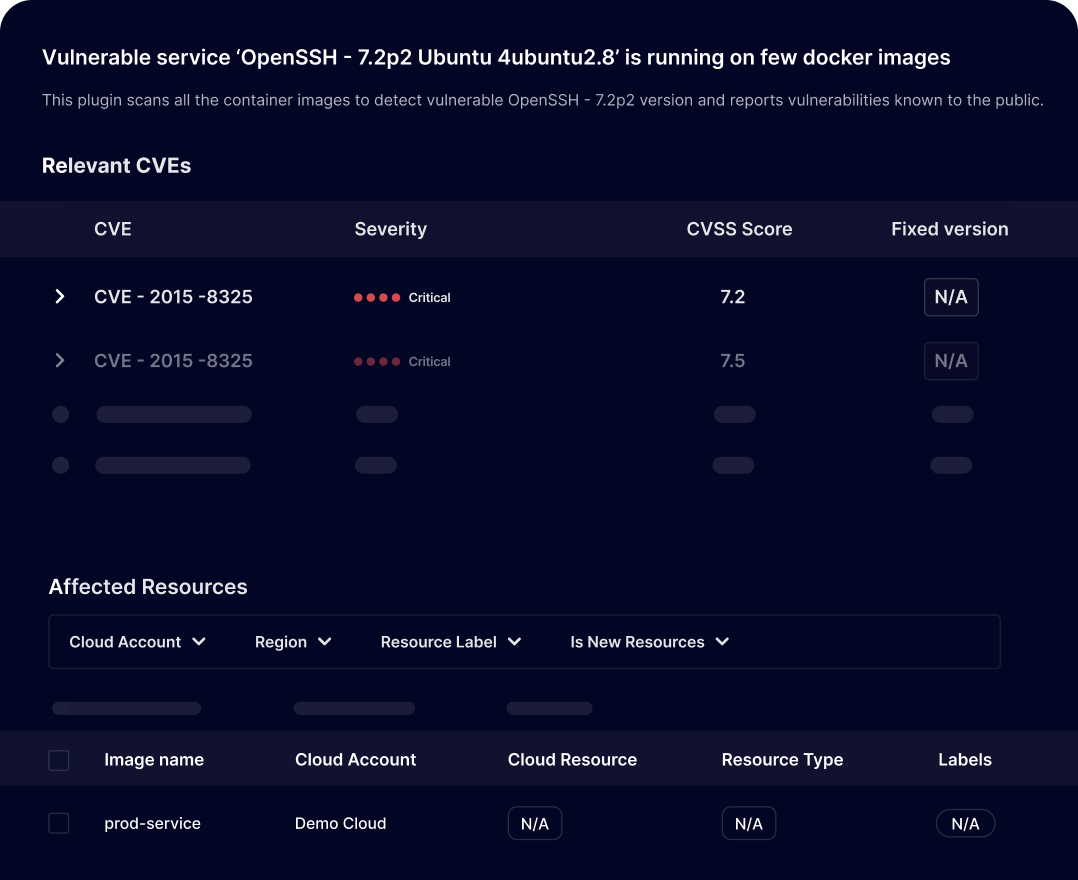
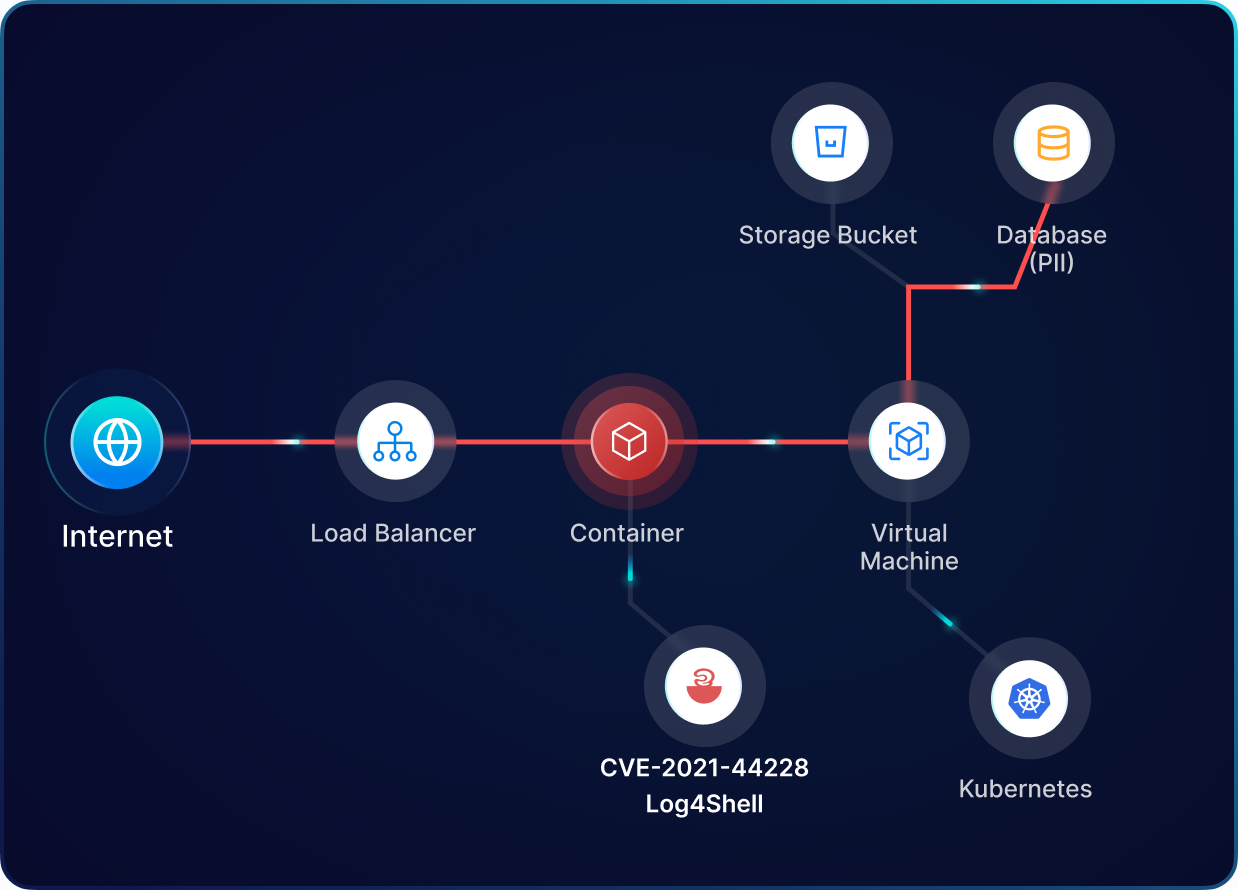
Complete security for Containers and Kubernetes clusters
Rapidly build and deploy containerized applications with our agentless security for containers and Kubernetes clusters without compromising on security.
Built by the team that has helped secure