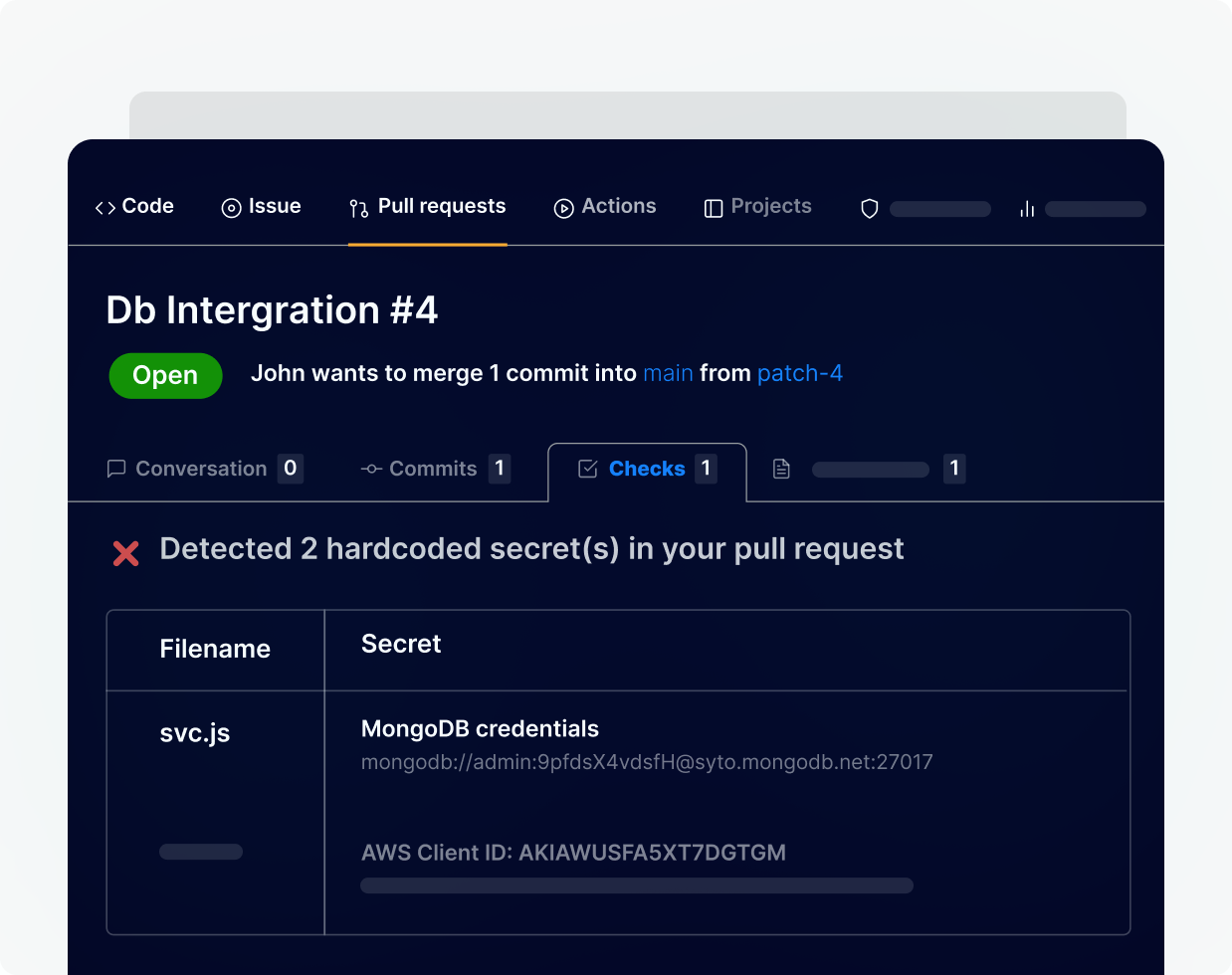
Ensure and enforce secrets-free source code
Real-time scanning to detect sensitive information and confidential data within your source code
Built by the team that has helped secure






Real-time scanning to detect sensitive information and confidential data within your source code
Built by the team that has helped secure






Handling sensitive information, such as passwords, API keys, encryption keys, and certificates, in an unsafe or careless manner, such as - storing secrets in plain text, sharing them through unsecured channels, or failing to update and rotate them properly.
Lack of end-to-end monitoring to detect secret leakage across your infrastructure (source code, environment files, etc.)
The ability to instantly identify the leak and fix it quickly is extremely important.
Limited to zero monitoring for leaked secrets beyond your cloud infrastructure.
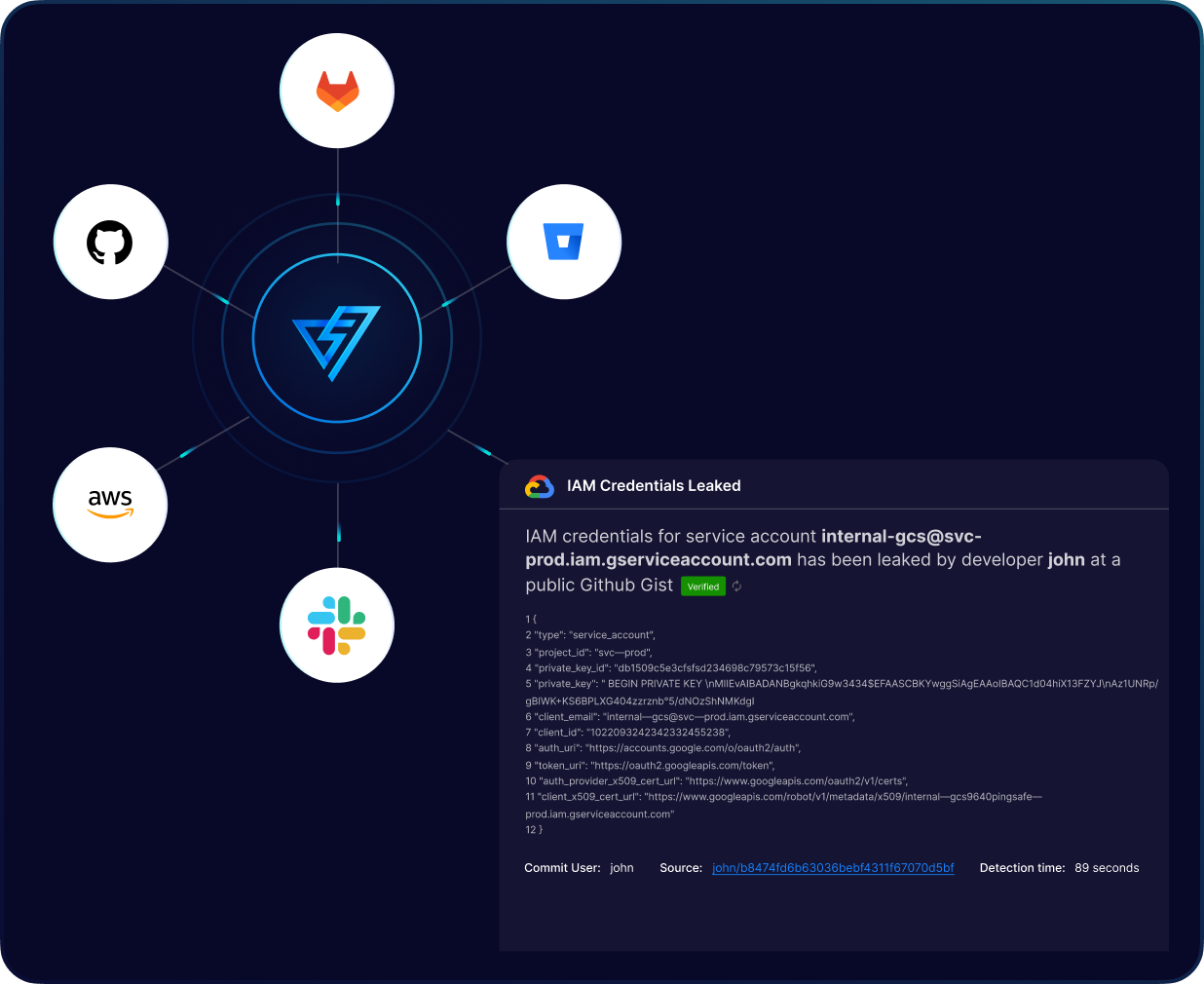
Our secret scanning engine offers advanced detection capabilities with the ability to identify and detect over 800 types of secrets and credentials in your code repositories.
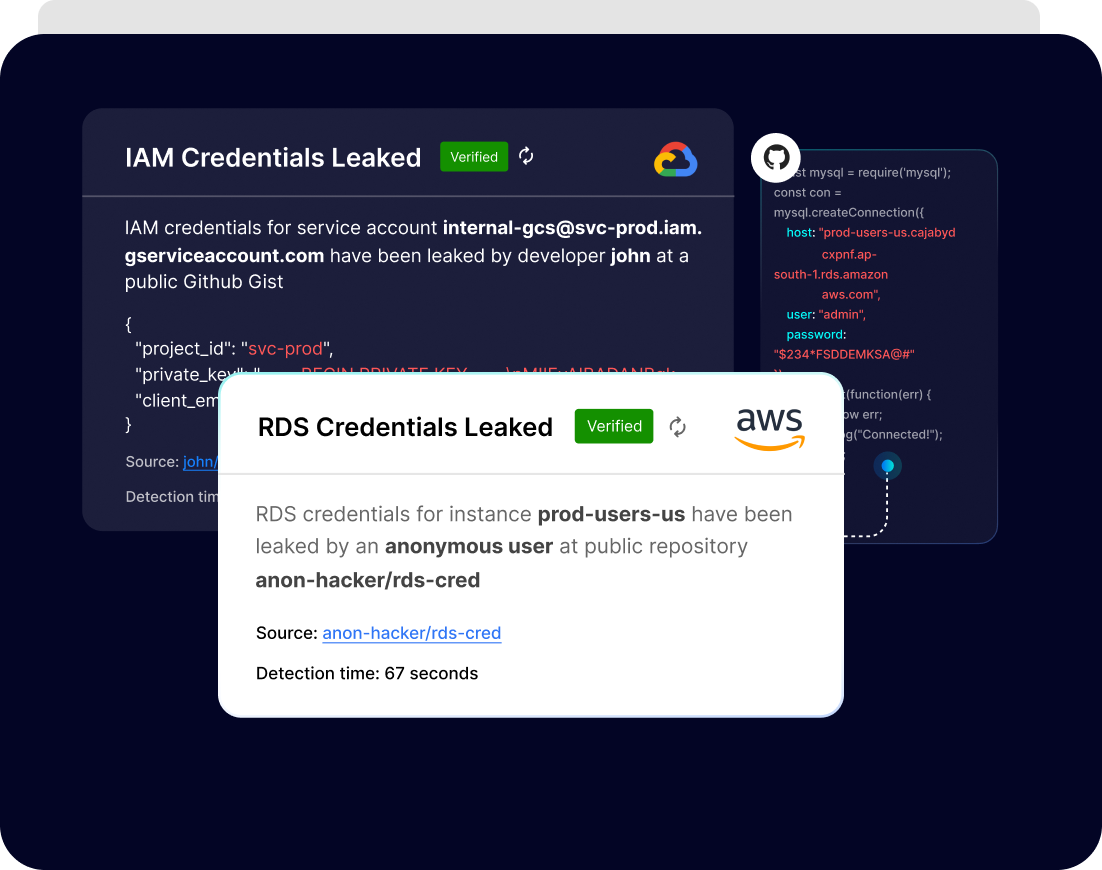
We provide complete monitoring of your entire organization's public and private repositories along with the public repositories of all developers within your organization. Our scanning engine also monitors gist files, which developers use to share code snippets amongst themselves, to ensure that there are no loose ends.
Our secret scanning engines continuously monitor all public repositories and instantly send an alert about any leaked secret across any public repository across the world to provide information about the source of the leak. This ensures that an organization is comprehensively covered from any secret being leaked by any random entity across any public repository.
Our solution offers instant detection and alerting within a minute of a secret being leaked, allowing immediate action to be taken to prevent and contain secret leakage and sprawl.
We don't just stop at identifying any leaked secret in your code but go a step further by restricting the code that contains any leaked secret to being merged. This enables Shift left Security practices where we focus on identifying such issues early in the deployment cycle to save organizations from any adverse future impact and future impact and enhance their developer’s productivity.






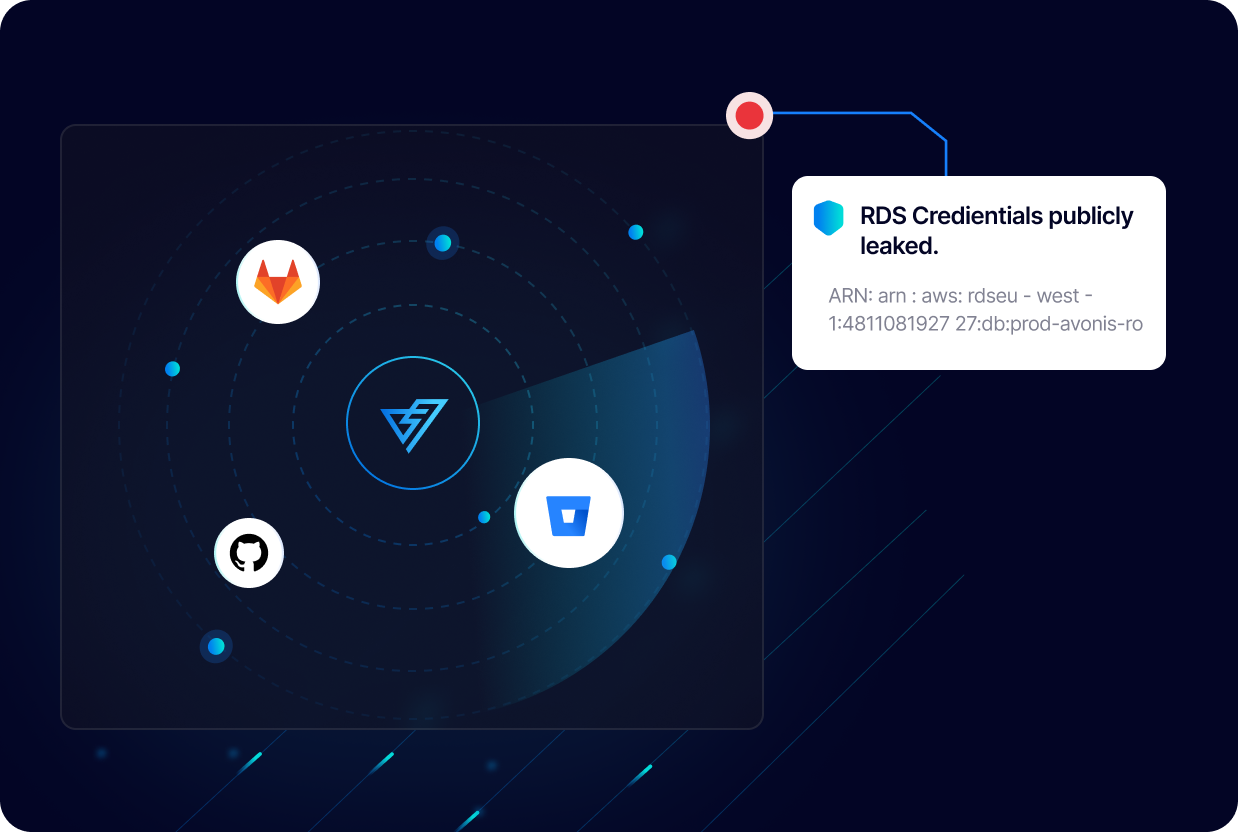
PingSafe provides continuous and real-time monitoring of your cloud environment to detect any leaked cloud credentials. Our solution will instantly alert you as soon as a leak is detected, allowing you to take immediate action to secure your data and prevent any potential breaches. PingSafe ensures that your sensitive data remains protected at all times.
PingSafe uses advanced algorithms to ensure no false positives. Only verified hardcoded secrets are reported. This eliminates the need for manual verification of alerts, saving valuable time and resources. You can trust that any alert received is a true indication of a hardcoded secret and can take action accordingly.
PingSafe’s Secret Scanning Engine is capable of recognising over 800+ types of secrets and cloud credentials that exist in code repositories across GitHub, GitLab and BitBucket. This intelligence is fuelled by our knowledge of scanning over 1.4 Billion commits to ensure we deliver the most reliable and robust results when it comes to detecting these secrets.
We offer integration with multiple CI/CD tools, alerting channels and workflow automation tools to ensure immediate action is taken upon detecting a potential threat. This feature allows for efficient and timely responses to potential breaches.