SentinelOne Completes Acquisition of PingSafe
Learn MoreModernize Cloud Security.
Outsmart Attackers.
Unparalleled protection for your multi-cloud infrastructure, from development to deployment.
Trusted by leading enterprises
Tackle your biggest cloud security challenges
PingSafe's unified platform has advanced components to safeguard your multi-cloud environment.
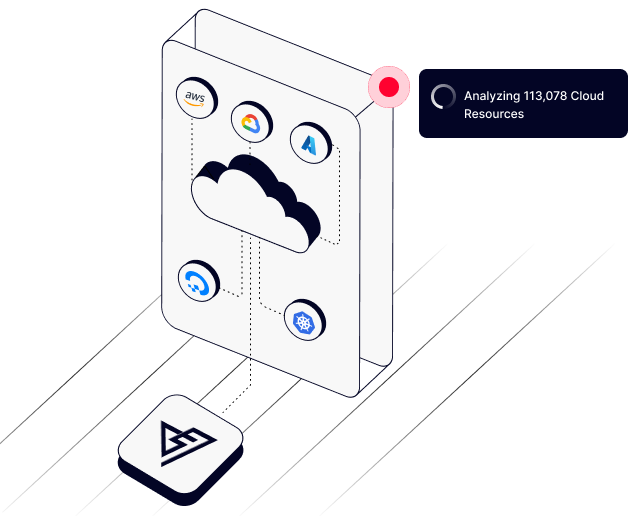
Single pane of glass view into your entire cloud estate. Automate your cloud compliance monitoring with PingSafe. Built-in gap analysis supports various standards like SOC2, PCI, HIPAA, and more.
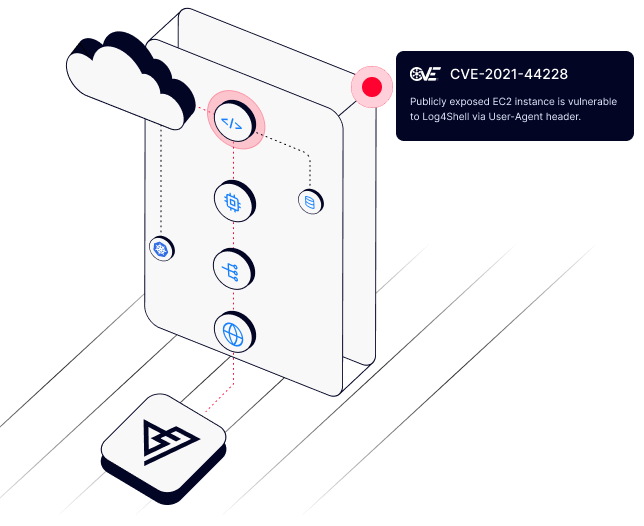
Don't overwhelm your security team with thousands of false critical vulnerabilities. With Offensive Security Engine, PingSafe's CNAPP platform helps your security team focus only on the ones which are truly exploitable.
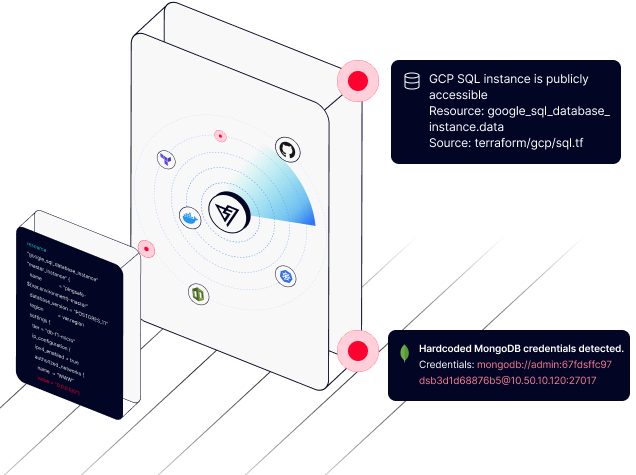
Breaches due to secret leakages can wreak havoc within an organization. PingSafe detects leaked credentials across public developer repositories and integrates directly into your CI/CD pipeline to provide complete coverage.

We make it easy for you to 'test early and test often.' PingSafe's CNAPP platform assists in creating processes for managing vulnerabilities early in your development cycle. Shift left with us.
Comprehensive cloud security through PingSafe's CNAPP



Compliance Monitoring
Cover all the essential tests required for compliance.
Learn Compliance Monitoring
Vulnerability Management
Agentless vulnerability management to secure your Cloud Workloads
Learn Vulnerability ManagementDon't just take it from us.
See what our customers say
Backed by the best
PingSafe is backed by leading venture capitalists who believe in our mission to redefine the spectrum of cloud security.
In the news