We use cookies to improve your browsing experience, personalize content, and enhance the use of our website. By clicking on the Accept button, you consent to the use of cookies on your device as described in our Privacy Policy.
Book a call with our solutions expert
Protect your cloud with our complete CNAPP
Proactively secure your cloud with unparalleled protection, from development to deployment.
Built by the team that has helped secure






How Does PingSafe Work?
PingSafe quickly scans your entire cloud infrastructure from an attacker's point of view. We then identify, prioritize and auto-remediate issues, to secure your business.

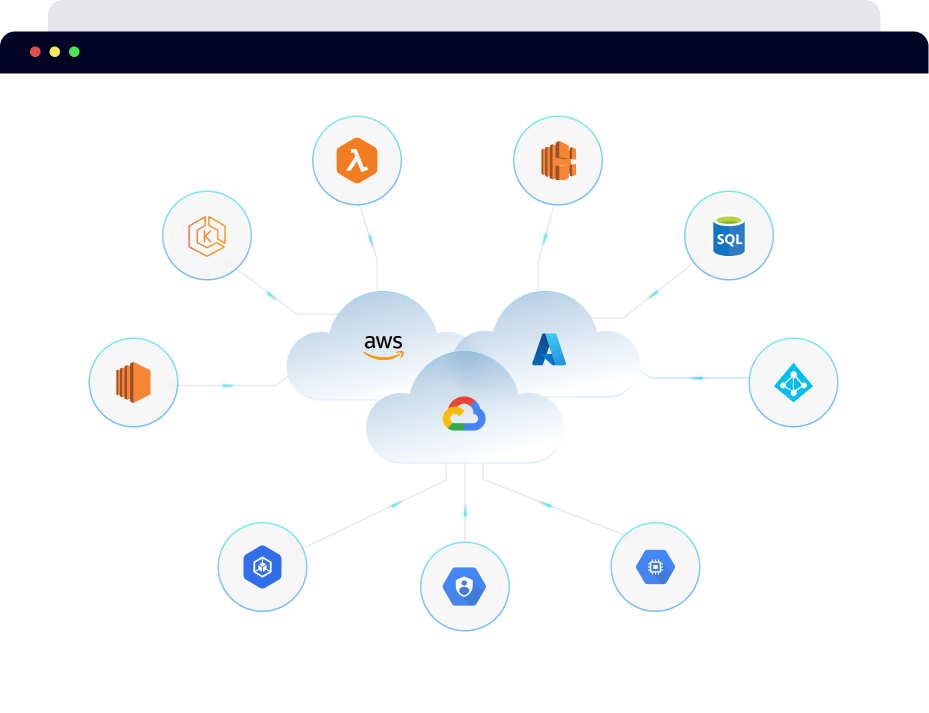


Onboard entire AWS organization, GCP organization, Azure Tenant, and DigitalOcean Teams in a go with PingSafe. Additionally, PingSafe can auto-detect and safeguard newly added cloud accounts. Get started on your cloud security journey in minutes!
Get Started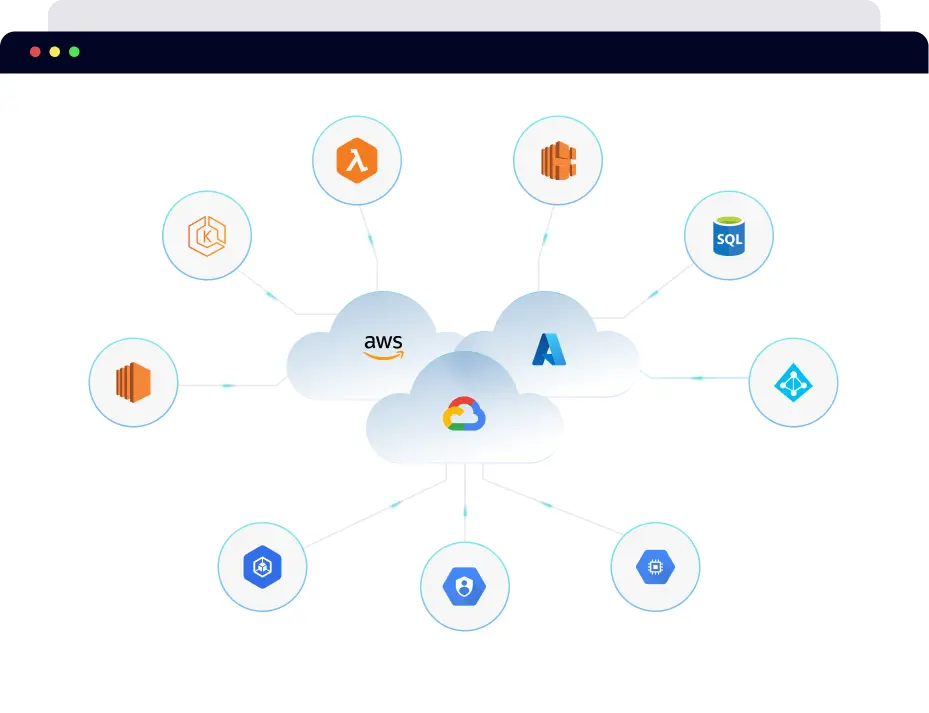
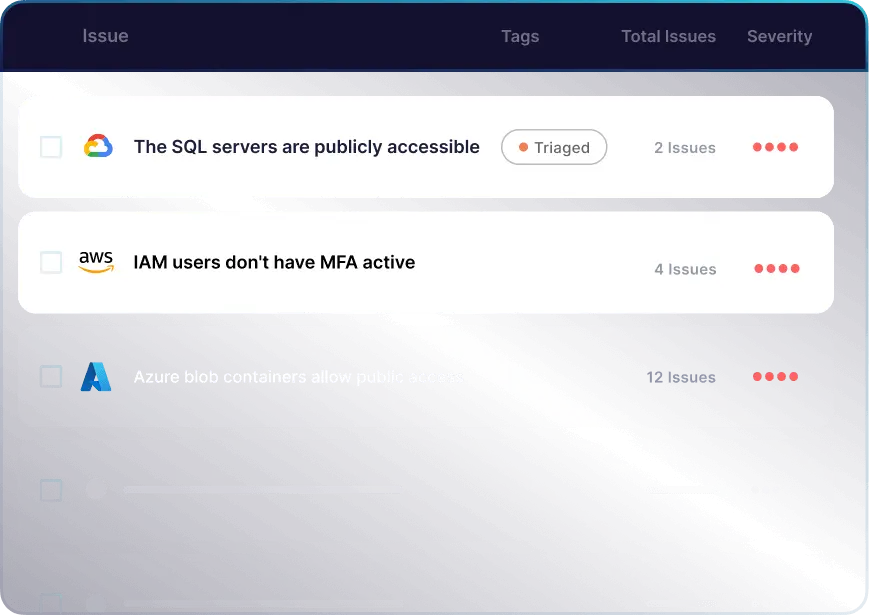
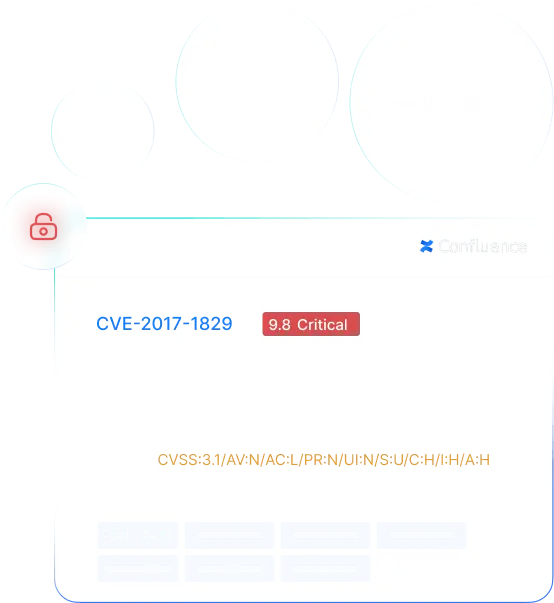
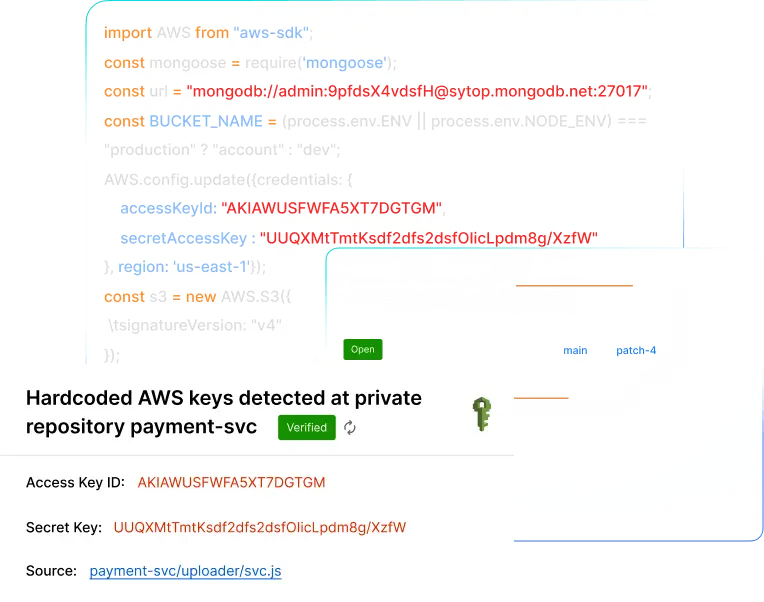
PingSafe checks multi-cloud resources (VMs, databases, containers, serverless) and monitors external events to detect risks like exposing cloud secrets in a public commit.
Get Started
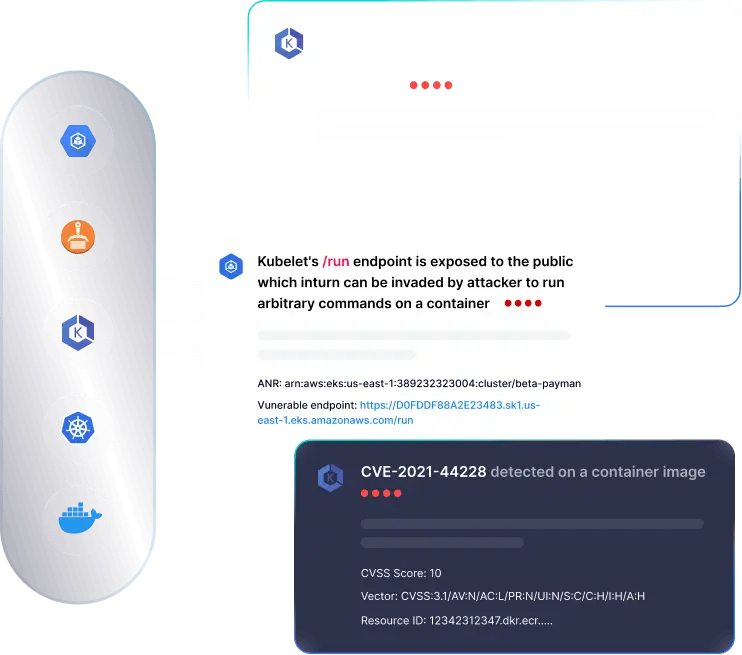
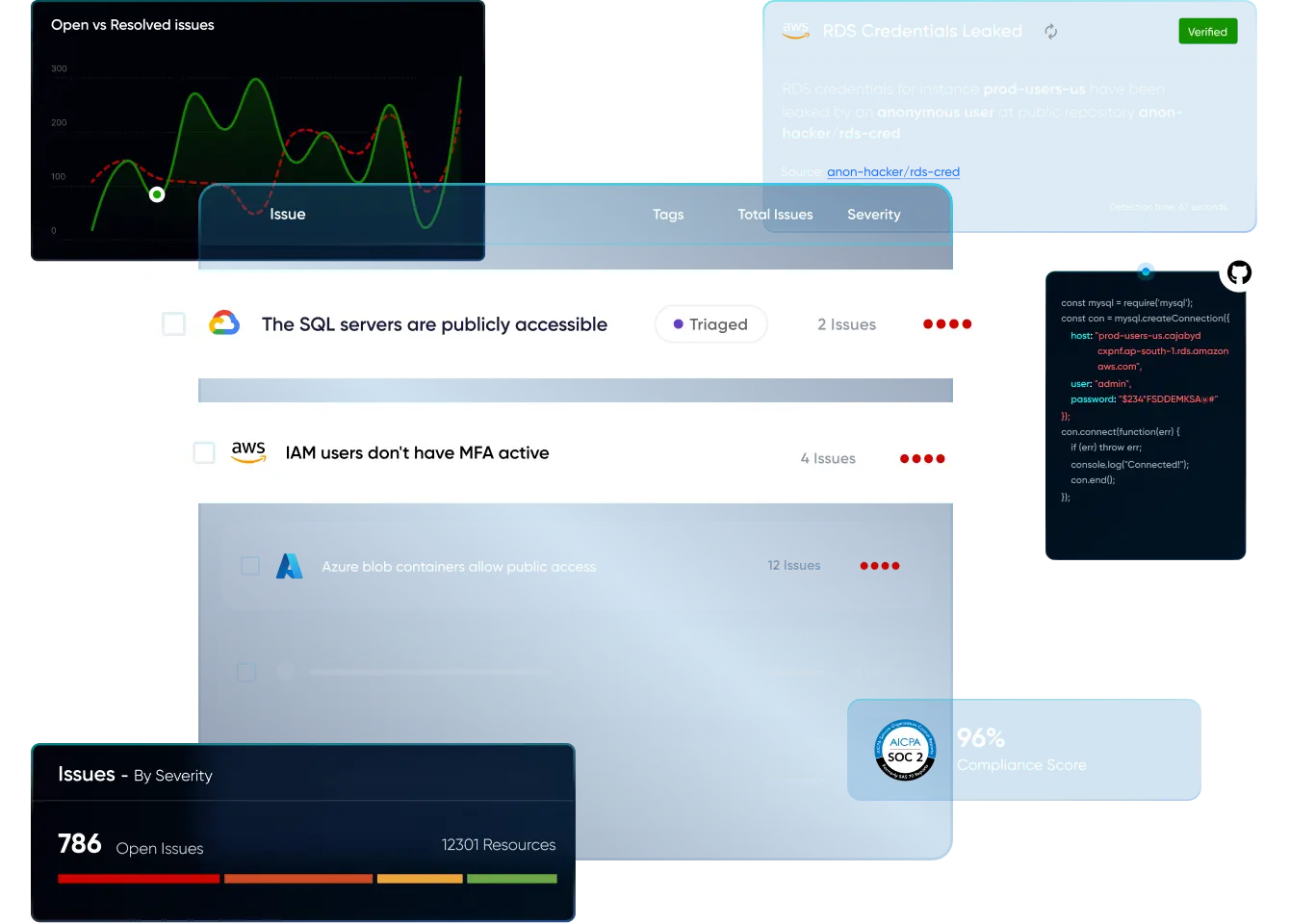
PingSafe deep cloud analysis helps in understanding complex relationships between your cloud assets and external events. This enables you to prioritize risks and understand lateral movement within your cloud, minimizing noise and improving threat visibility.
Get Started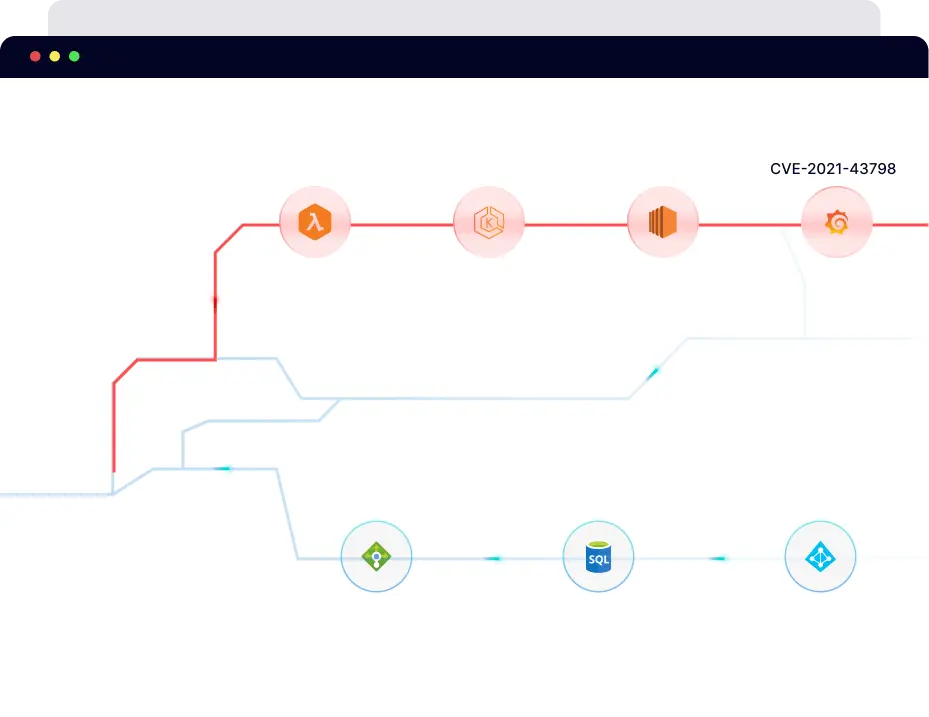
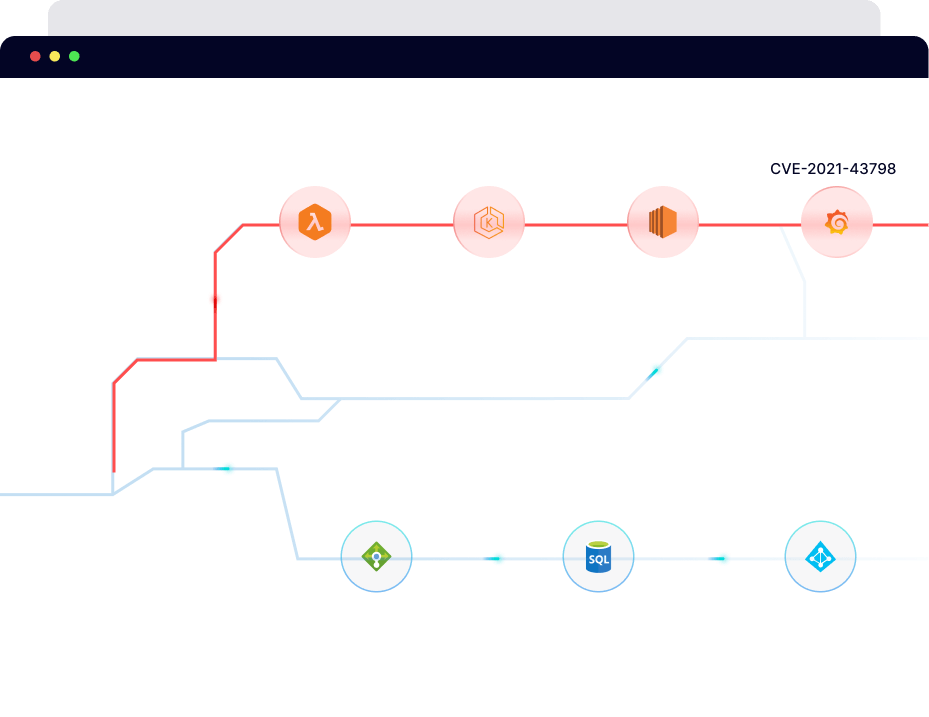
Leverage PingSafe's Offensive Security Engine to precisely identify cloud vulnerabilities that lets you assess threat exploitability with our visual hacker graph.
Get Started
PingSafe sends detected threat findings and auto-remediates misconfigurations in real-time, in line with defined workflows, via preferred integration channels (like JIRA, Slack, PagerDuty, Email, Sumo Logic, Splunk, OpsGenie, and more).
Get StartedOne Platform. Many Solutions
Why Choose PingSafe?
Transform your cloud security using our unique Offensive Security approach.

Engineered by Cloud Security Experts
Built by renowned white hat hackers that have secured leading companies, including Meta, Uber, Twitter, LinkedIn, and Salesforce.
API-Based Agentless Onboarding
Onboard all your cloud accounts in a single step using PingSafe’s easy-to-use IaC templates. No agents needed.
Multi-Cloud Support
Compatible with multiple cloud partners, including AWS, GCP, Azure, and DigitalOcean.
PingSafe Hacker Graph
Engineered with an attacker’s mindset, PingSafe gives you a visual representation of your cloud infrastructure, depicting the exploitability of threats.
Auto-remediation
Auto-eliminate misconfigurations in your cloud with customized workflows.
Major Compliances Monitoring
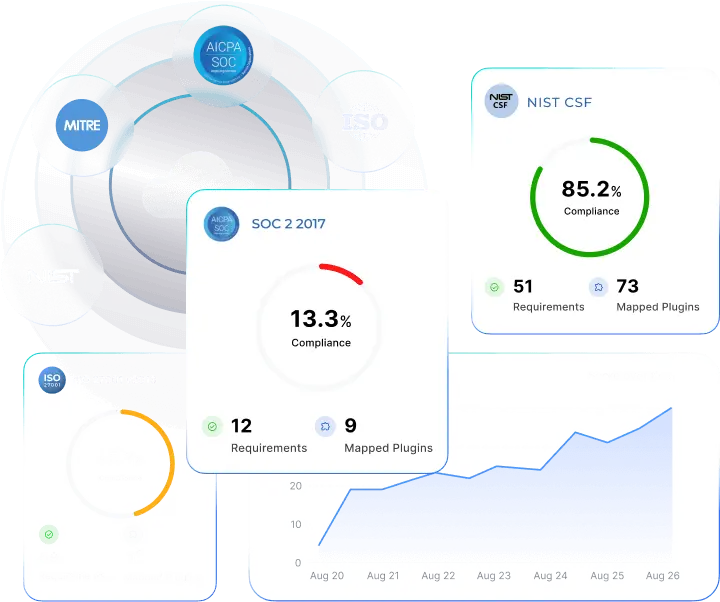
Built-in capability to perform a gap analysis of standard compliances (CIS, PCI-DSS, HIPAA, and RBI Compliance) in your cloud environments.
Single Platform, Multiple Integrations
Connect your preferred collaboration tools to get real-time alerts.
Shift Left Security
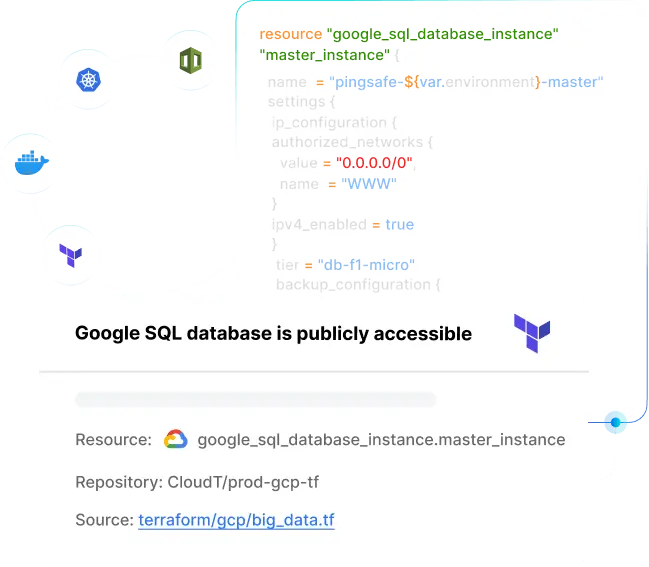
Adopt security early in your development process by using PingSafe’s IaC, Docker image scanning, and secret scanners.
Don't just take it from us.
See what our customers say
"Our security team loves PingSafe because it lets them focus on what's important."
Prashant Borde
Engineering Leader, Stripe

"PingSafe's CNAPP platform is significantly less noisy and its alerts are more actionable as compared to alternatives."

Daniel Wong
CISO, Skyflow, Inc.

"PingSafe's CNAPP platform and its capability to provide proof of exploitability made it super easy for us to choose it over other alternatives."

Hari
VP Engineering at Near Intelligence (Nasdaq:NIR)

"PingSafe is an excellent solution for dynamic and real-time monitoring of all the multi-cloud workloads. The flexibility of configuration and the ease of maintenance is a big plus."

Subhajit Deb
Global CISO, Envoy Global, Inc.

Ready to see PingSafe in action?
We've said enough. It's time to see for yourself.