Secure your cloud credentials beyond your cloud infrastructure
Built by the team that has helped secure






Built by the team that has helped secure






Developers often commit secrets in public repositories for POC exercises, Hackathon events, etc. and forget to rotate them.
Lack of monitoring of all developers’ personal repositories of an organization for leaked secrets.
The ability to identify the leak and fix it instantly is extremely important.
Beyond your cloud infrastructure.
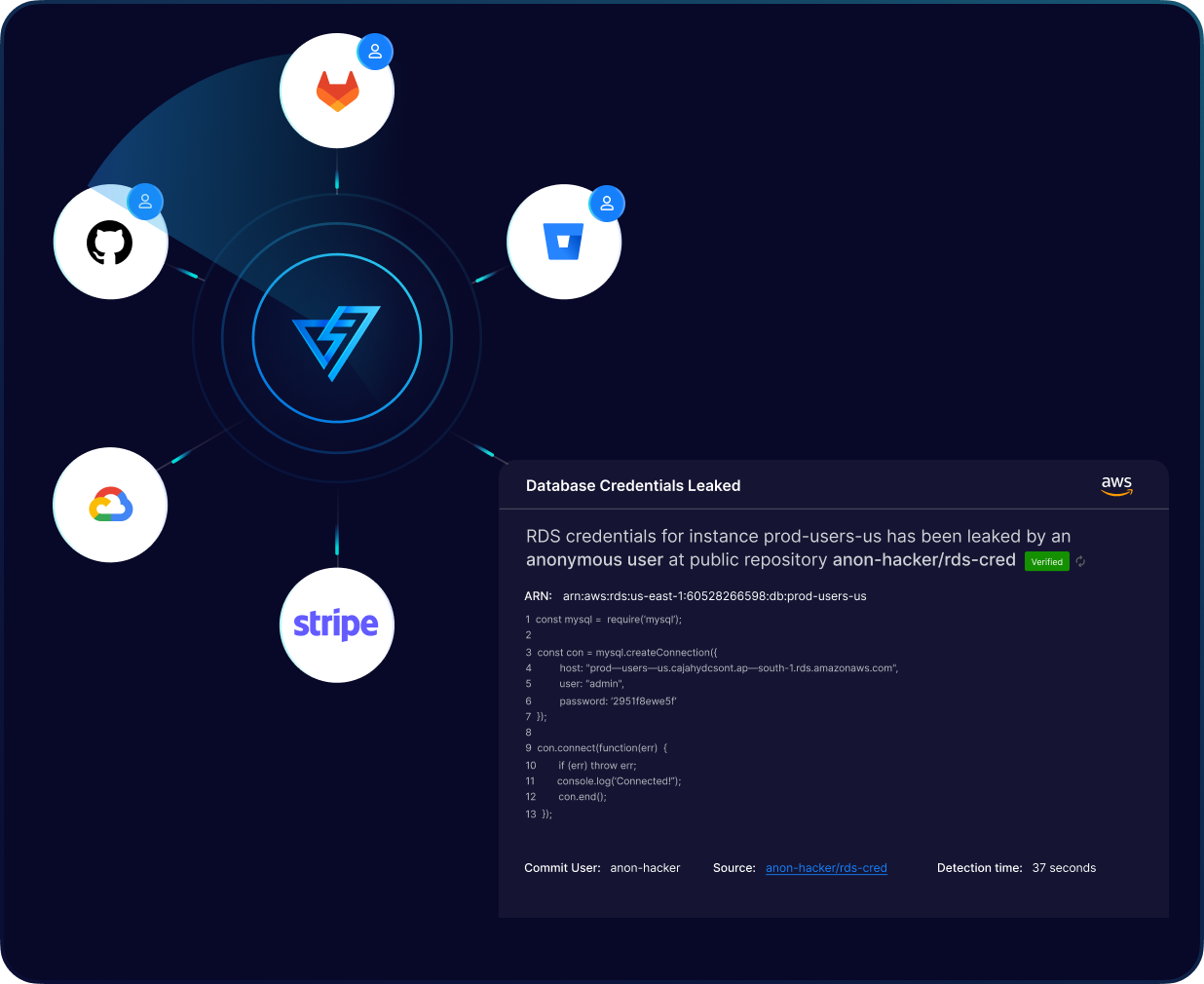
PingSafe analyzes more than 10 million events per day across all public repositories to detect and prevent cloud credential leakage. This proactive approach helps secure sensitive information and prevent unauthorized access.
Our solution provides end-to-end developer oversight by monitoring all developers' personal repositories within an organization for secrets. This ensures that cloud credential leakage is detected early, preventing unauthorized access to sensitive information.
Our solution offers instant detection and alerting within a minute of a secret being leaked, allowing for immediate action to be taken to prevent and contain cloud credential leakage.




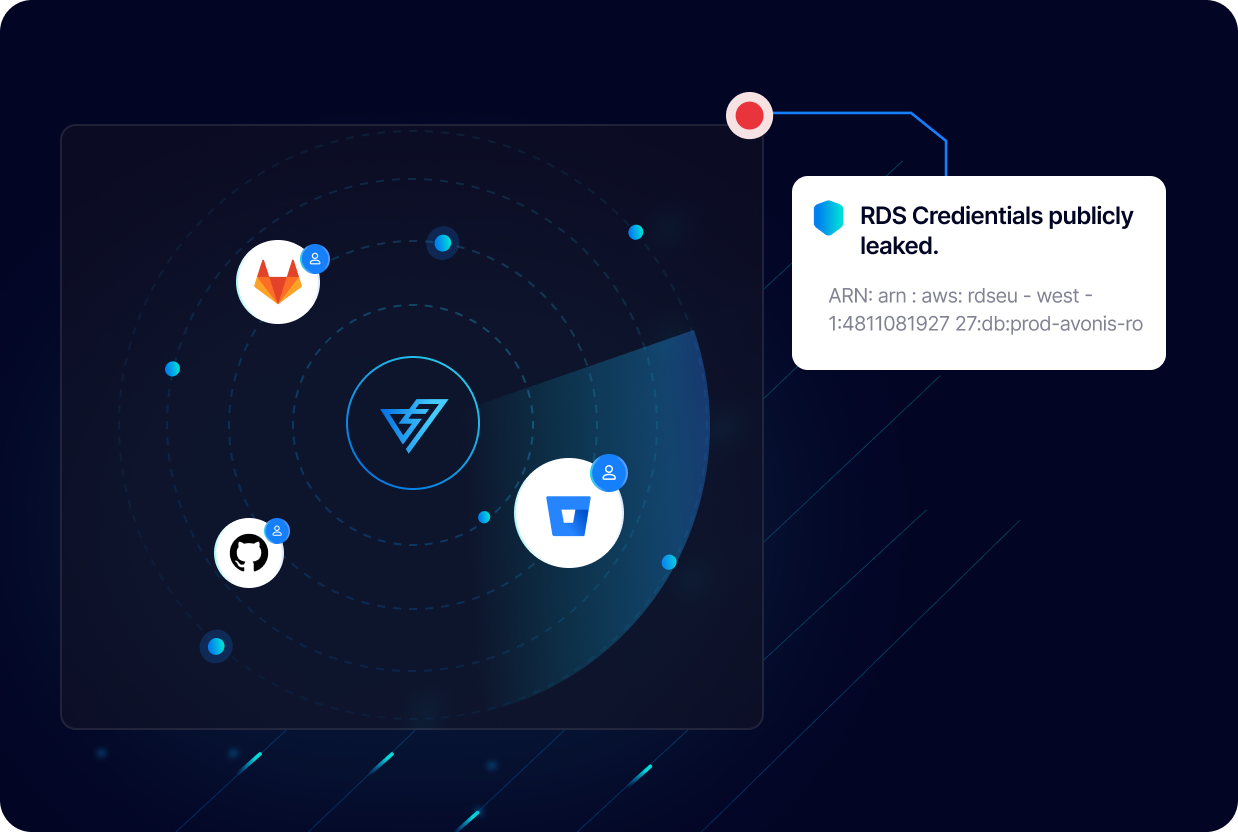
PingSafe provides continuous and real-time monitoring of your cloud environment to detect any leaked cloud credentials. Our solution will instantly alert you as soon as a leak is detected, allowing you to take immediate action to secure your data and prevent any potential breaches. PingSafe ensures that your sensitive data remains protected at all times.
PingSafe uses advanced algorithms to ensure no false positives. Only verified leaked secrets are reported. This eliminates the need for manual verification of alerts, saving valuable time and resources. You can trust that any alert received is a true indication of a leaked secret and can take action accordingly.
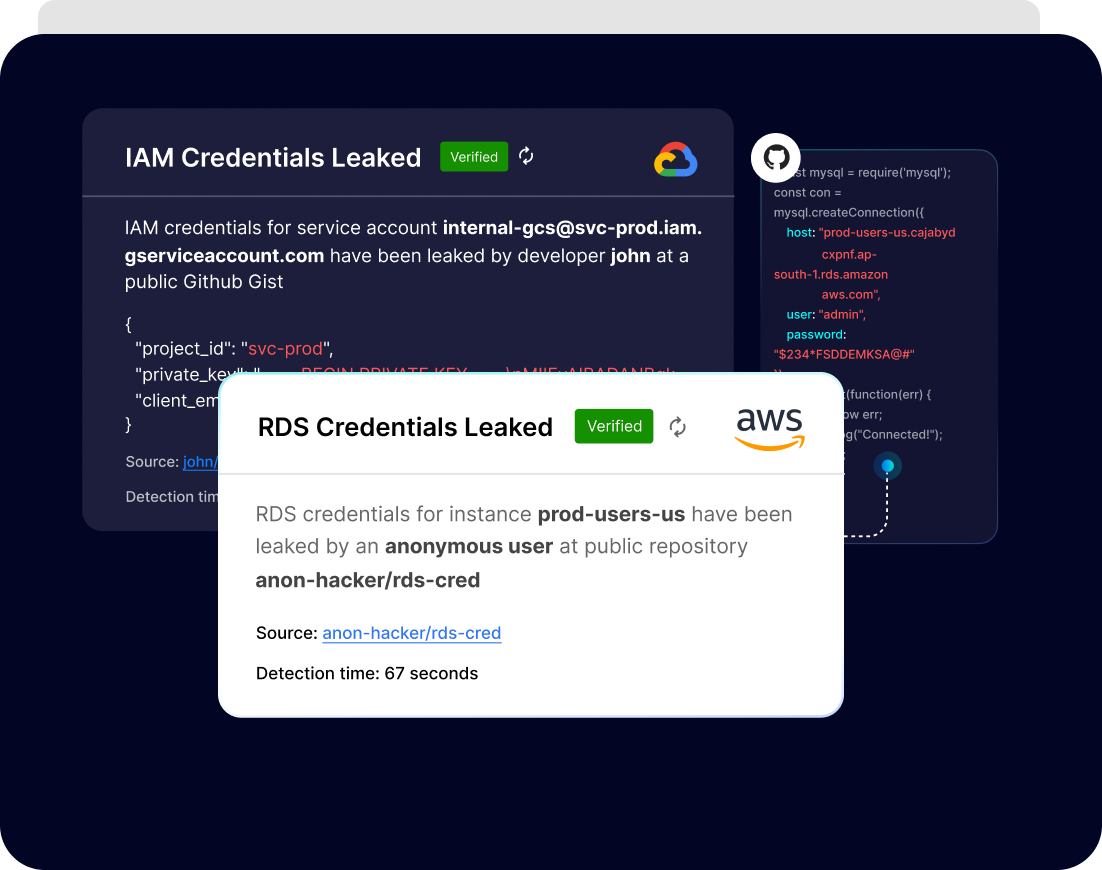
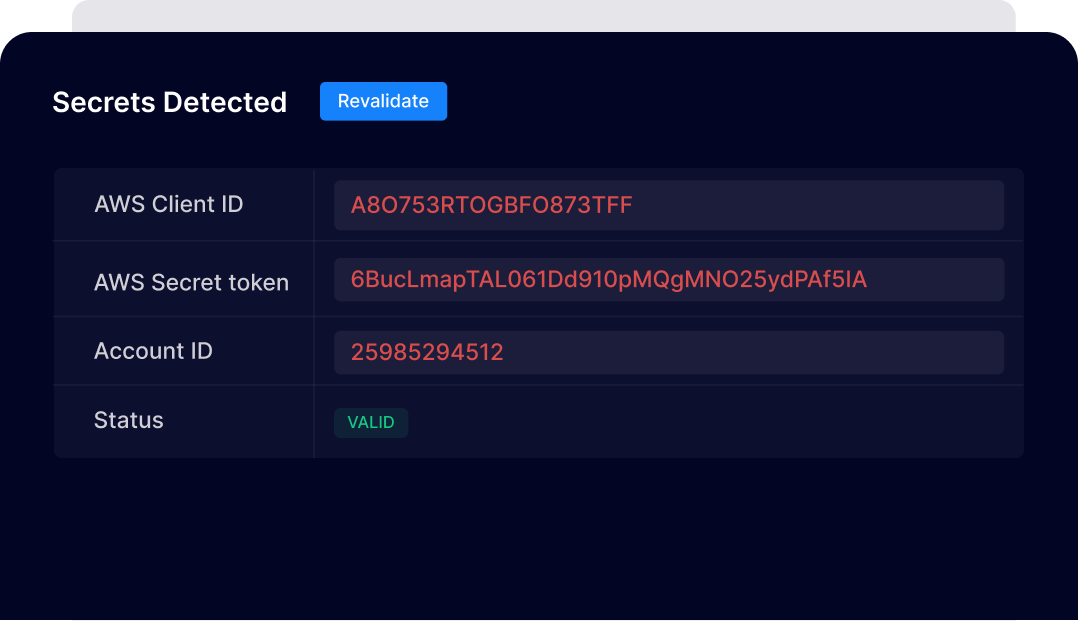
We detect cloud credential leakage by providing the ability to verify the validity of leaked secrets. This means you can trust that the information being leaked is authentic and accurate, allowing you to take quick and effective action to prevent unauthorized access.
We offer integration with multiple alerting channels and workflow automation tools to ensure immediate action is taken upon detecting a potential threat. This feature allows for efficient and timely responses to potential breaches.
